In any acquisition, early diligence work establishes the foundation for deal success. Before integration planning or capital allocation, buyers need clarity around the investment thesis, the people involved, and the security controls that protect operations. These five initial steps help investors reduce risk, improve valuation accuracy, and prepare for post-close execution. See also Questions in M&A: Common Challenges Explained. You can also find a more comprehensive checklist here.
1. Understand the Investment Thesis
Effective duediligence begins with strategic alignment. Before evaluating systems, staff, or cybersecurity exposure, the buyer must understand why the business is being acquired and how value will be created.
Is the acquisition about market expansion, operational efficiency, product scaling, or cost rationalization? Moreover, understanding the timeline and expected growth curve will determine the level of IT investment and the urgency of upgrades during the first 12–24 months.
2. Meet the People and Understand All Stakeholders
Acquisitions succeed when people support the objective. Therefore, early in diligence, meet the internal stakeholders who manage technology, security, finance, compliance, and day-to-day operations.
These discussions surface:
- key decision-makers
- institutional knowledge
- dependency risk
- undocumented workflows
- resource gaps
Additionally, understanding cultural alignment helps determine whether the target organization can support transformation at the expected pace.
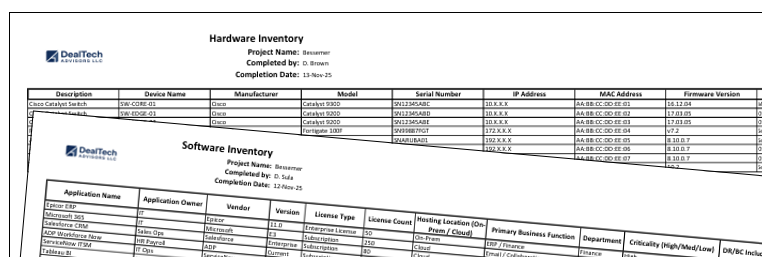
3. Inventory the Existing Landscape (Hardware and Software)
A comprehensive technology inventory is fundamental to IT due diligence. Buyers need full visibility into:
- servers, network gear, firewalls, and storage
- laptops, endpoints, and mobile devices
- operating systems, patch levels, and versioning
- licensed software and SaaS applications
This inventory becomes the baseline for cost modeling, lifecycle planning, and platform scalability. Furthermore, it helps identify what is secure, what is outdated, and what may require capital investment post-close. See also risks involved in IT Documentation Gaps in M&A: Key Considerations
4. Define the Physical Security
Due diligence must evaluate physical security controls, not just software controls. Buyers should confirm how offices, server rooms, wiring closets, and network equipment are protected.
Relevant considerations include:
- access-badge or biometric entry
- locked racks and restricted zones
- visitor logging
- surveillance
- fire, power, and environmental controls
These controls support business continuity and reduce the likelihood of operational disruption. Learn more about security threats in Legacy IT Risks in Private Equity Transactions
5. Schedule a Security Audit Incorporating a Threat Analysis
A third-party security audit with a formal threat analysis validates the cybersecurity posture early. This assessment identifies vulnerabilities, evaluates compliance exposure, and highlights potential breach pathways, thereby improving your understanding of potential risks.
The threat analysis helps quantify cyber-risk and aligns security spending with the investment thesis. Early audits prevent Day One surprises and protect deal value.
Closing Thought These five steps convert uncertainty into insight. By aligning with the investment thesis, meeting stakeholders, performing a technology inventory, validating physical security, and commissioning a threat-focused audit, buyers give themselves a stronger position for valuation accuracy, integration planning, and long-term scale.

Pingback: Questions in M&A: Common Challenges Explained
Pingback: IT Documentation Gaps in M&A: Key Considerations
Pingback: 100-Day IT Playbook for Effective Execution
Pingback: 5 Critical IT Actions for a Successful Carve-Out
Pingback: IT due diligence checklist private equity